Passwd
change user password
Syntax
passwd [options] [username]Example
To change the password for the current user, simply run:
passwdYou will be prompted to enter and confirm the new password.
If changing the password for another user, use:
sudo passwd usernameReplace
usernamewith the actual username.
Pwquality.conf
The pwquality.conf file in Red Hat Enterprise Linux (RHEL) is used to configure password quality requirements. It is part of the Pluggable Authentication Modules (PAM) system and is often used to enforce password complexity rules. As a sysadmin, you can use this file to enhance the security of user passwords.

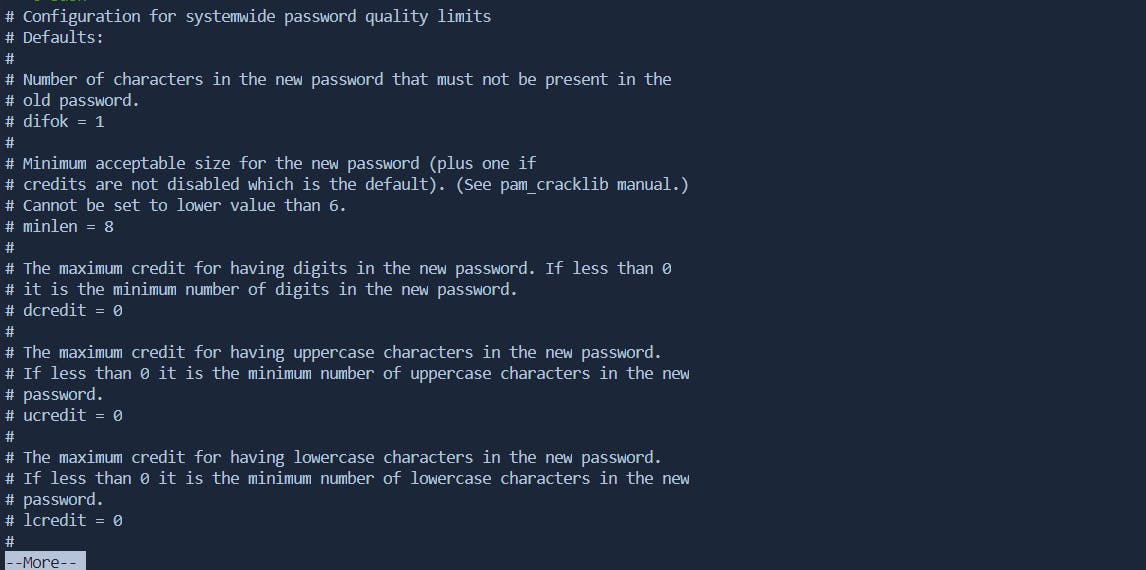
Enforcing Minimum Password Length
Let's say you want to ensure that all users have passwords with a minimum length of 10 characters.
Edit the
pwquality.conffile:sudo nano /etc/security/pwquality.confAdd the following line:
minlen = 10Save the file.
Now, users attempting to change their password or set a new one will be required to use a password with a minimum length of 10 characters.
Enforcing Password Complexity
You want to enhance password security by requiring users to include characters from different character classes (upper-case, lower-case, numeric, and special characters).
Edit the
pwquality.conffile:sudo nano /etc/security/pwquality.confAdd the following lines:
minclass = 4 minclassrepeat = 3Save the file.
Now, when users change or set their password, they will be prompted to include characters from at least four different character classes, with no more than three characters from the same class in a row.
Denying Simple or Common Passwords
To prevent users from using simple or common passwords, you can use the
minclassandminclassrepeatparameters along with dictionaries.Install a password dictionary package (e.g.,
cracklib-dicts):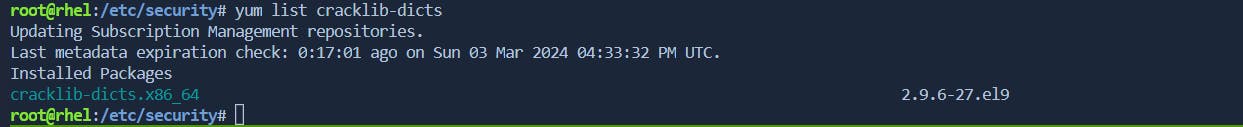
sudo yum install cracklib-dictsEdit the
pwquality.conffile:sudo nano /etc/security/pwquality.confAdd the following lines:
minclass = 4 minclassrepeat = 3 dictcheck = 1Save the file.
With these settings, users attempting to change their password will be denied if their new password is found in the dictionary.
Note:
Always test changes in a safe environment before applying them to a production system. Additionally, consult the
pwquality.confman page (man pwquality.conf) for a comprehensive list of configuration options and details.
Encryption [/etc/shadow]
user passwords are stored in the /etc/shadow file. The /etc/shadow file contains encrypted password information, among other user-related data. When a user account does not have a password set, you might observe two exclamation marks ("!!") in the password field in the /etc/shadow file.
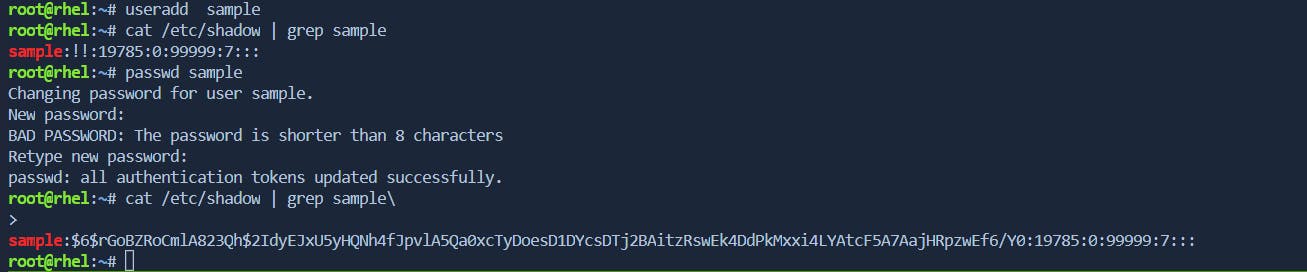
Crypt function
passwd command to reset a password, it utilizes cryptographic functions to securely store the password. The hashing function, typically the crypt function, is used to encrypt the password and store it in the /etc/shadow file.
using openssl and salt combination to generate encrypted key passwd
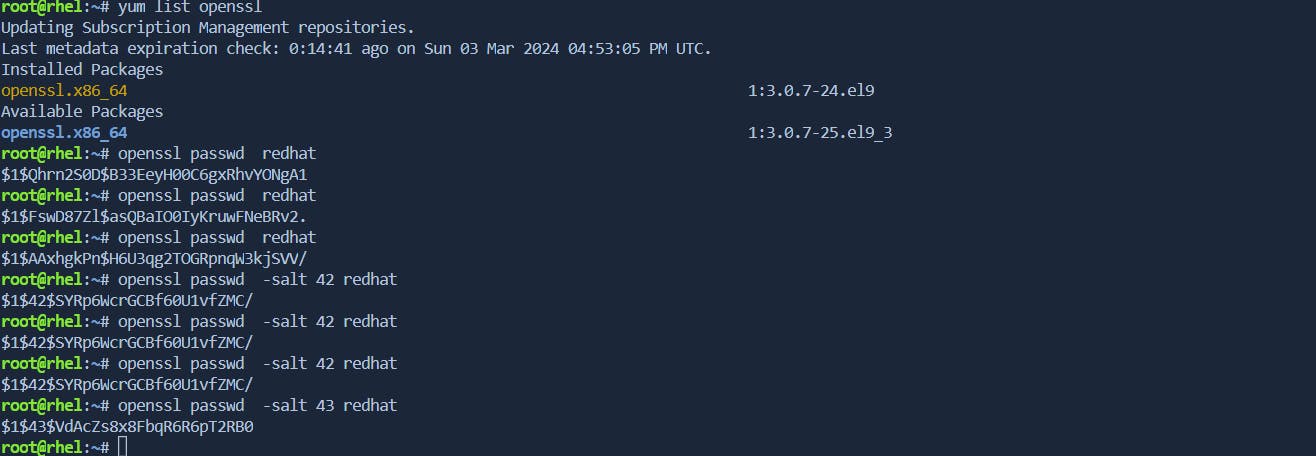
https://man7.org/linux/man-pages/man3/crypt.3.html
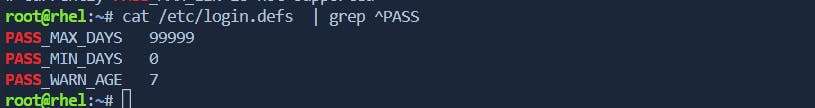
Note:- if we want to create user with default max/min/age of password we can define in below file
| Feature | /etc/login.defs | pwquality.conf |
| Primary Focus | General login behavior | Password complexity |
| Options | Minimum length, aging, warnings | Character classes, reuse prevention |
| Enforcement | Default system-wide settings | Defines complexity requirements |
Chage
The chage command in Linux is used to modify user password aging information, which is stored in the /etc/shadow file. It allows a system administrator to set and change the aging policy for user accounts.
1. View Current Password Aging Information:
chage -l username
This command displays the current password aging information for a specific user (username). It includes details such as the last password change date, password expiration date, and other aging-related settings.
2. Set Maximum Password Age:
sudo chage -M 90 username
This example sets the maximum number of days a password is valid for the user username to 90. After 90 days, the user will be prompted to change their password.
3. Set Password Expiry Date:
sudo chage -E 2024-12-31 username
This command sets the password expiration date for the user username to December 31, 2024. After this date, the user will be required to change their password during the next login.
4. Set Password Inactivity Period:
sudo chage -I 14 username
This example sets the number of days of inactivity allowed for the user username to 14. If the user does not log in within this period, their password will expire.
5. Disable Password Aging:
sudo chage -m 0 -M 99999 -I -1 -E -1 username
This command disables all aging-related features for the user username. It sets the minimum and maximum password ages to 0 and 99999, respectively, and disables inactivity and expiration.
6. Set Warning Period:
sudo chage -W 7 username
This example sets the number of days before password expiration that the user username will start receiving warning messages. In this case, warnings will be displayed 7 days before password expiration.Note:
Note
The
-Mflag sets the maximum number of days between password changes.The
-Eflag sets the date on which the password will expire.The
-Iflag sets the number of days of inactivity allowed before the account is locked.The
-mflag sets the minimum number of days between password changes.The
-Wflag sets the number of days of warning before password expiration.visudo ----> /etc/sudoers
vipw ----> /etc/passwd
vigr ----> /etc/group